


|
SSO instructions Steps to onboard a new customer for SSO configuration.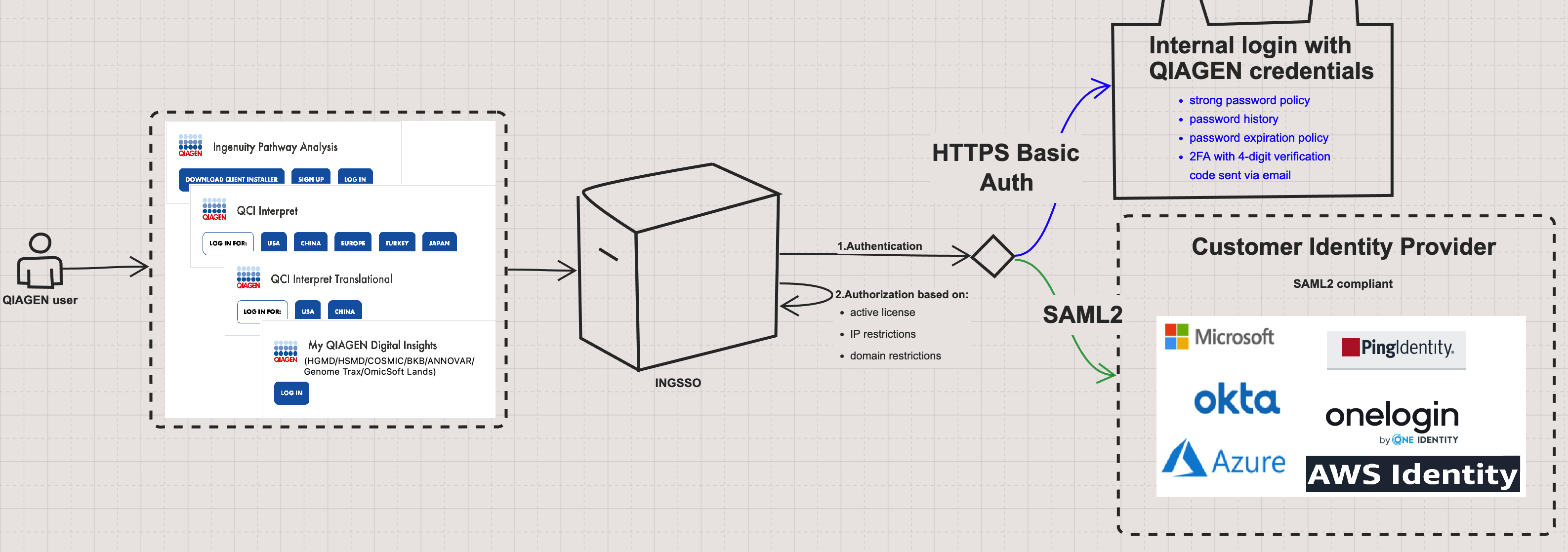
Follow these steps to get onboarded for SSO: 1. The organization’s IT department formally requests Single Sign-On (SSO) integration with QIAGEN Digital Insights (QDI) through QDI Customer Support. QDI Customer Support then provides the requirements for SAML-based SSO integration. The <NameID> is a required element in the SAML authentication response, which must also include the following claims: email address, first name, and last name.2. QDI Customer Support provides the organization’s IT department with a list of SSO-supported products licensed to the organization, along with the domains whitelisted under those licenses and the users covered by them. Based on this user list, QDI Support notifies the IT department if any inconsistencies are found in the username portion of the email addresses, as these could potentially lead to failed SSO logins.3. The organization’s IT department confirms which domains use the same identity provider. Only domains that share a common identity provider can be included in a single SSO configuration. If a license involves multiple identity providers, a separate SSO integration must be set up for each one.4. When an organization has a license for multiple SSO-supported products, QDI Customer Support informs the license administrator(s) that SSO integration applies to all products collectively; it cannot be enabled for only a subset of these products. However, SSO can be deactivated on a per-user basis if needed.5. The organization's license administrator(s) confirm the QDI products covered in the SSO integration.6. QDI Customer Support registers a representative from the organization’s IT team as the SSO administrator. This administrator is responsible for configuring the SSO integration through the SSO Configuration page in the QDI Admin Tool. To streamline the setup, the organization's IT team is encouraged to share the Identity Provider (IdP) metadata XML with the QDI Customer Support for validation. The Service Provider (SP) metadata XML can be downloaded directly from the SSO Configuration page.7. After the SSO configuration is completed, the organization’s IT team informs internal users about the implementation, schedules the switchover to SSO at a time that avoids disrupting ongoing analyses, and provides ongoing support for authentication-related issues.How to use login with SSO.Please visit this Frequently Asked Questions
Q - Which are the supported protocols to implement SSO?
Q - Is SSO available for all QIAGEN Digital Insights applications?
Q - Can I turn on SSO for product A but not for product B?
Q – My institution has multiple licenses. Can some licenses be exempt from SSO?
Q - Can the license administrator add/remove users from SSO?
Q - Do we need to purchase a license before implementing SSO?
Q - Is there an extra licensing cost for SSO?
Q - Is auto user provisioning available with QIAGEN Digital Insights SSO?
Q – Who is responsible for user authentication issues?
Q – Will SSO continue to work when a QIAGEN Digital Insights product license has expired?
Q – Can we self-configure the domain or re-upload XML, or enable/disable SSO?
Q – Will IP address restrictions on the license be enforced?
Q – Can individual user accounts be exempt from SSO?
Q – Can we continue to use the QIAGEN Digital Insights Admin Tool?
Q – Can different SSO configurations be provided for the same domain in situations where QDI products are hosted on different data centers located in different countries?
Q – Should the Service Provider certificate be asserted?
Q - Why am I getting a message that my user account could not be found in the system after logging in via SSO?
Q - Which SAML/Identity Provider do you use?
Q - Will the SAML Authentication request be encrypted, and should the SAML response be encrypted?
Q - Can encryption be turned off during development to debug?
Q - Do you support metadata exchange (SP sends metadata to IdP, IdP creates a connection, IdP sends metadata, SP imports metadata, turn testers loose)?
Q - Is IdP-initiated SSO required, or can you support SP-initiated SSO?
Q - What attributes are required, and what is the SAML_Subject? The Employee username, employee ID, something else?
Q - Is the application integrated with AD? Do users use their network credentials or something else to log in?
Q - If you SSO the application, what happens to existing user accounts? Are they merged or something else?
Q - What is the user experience, with SSO enabled, for a user who’s not set up in the application yet?
Q - Do users access the application via a public/shared/training type workstation that they are not personally logged into?
Q - Do users require the ability to log in with different credentials for test/developer/admin access?
Q - Do you have any MFA requirements?
Q - What should the user log-out experience look like?
Q - Do we need a log-out button?
Q - Are you receiving any kind of feed of users' information from CCF? If so, what is the purpose of it, and how will SSO via SAML affect that (or vice-versa)?
Q - Are there any scripts or programs that access the application using a userid/PW?
Q - Is SSO enabled in your Test/Staging environment?
Q - If this is internally hosted, do you have your certificate(s) set up? SSO known limitations
SSO work flows that require special attention
|
|
|